Surface Area
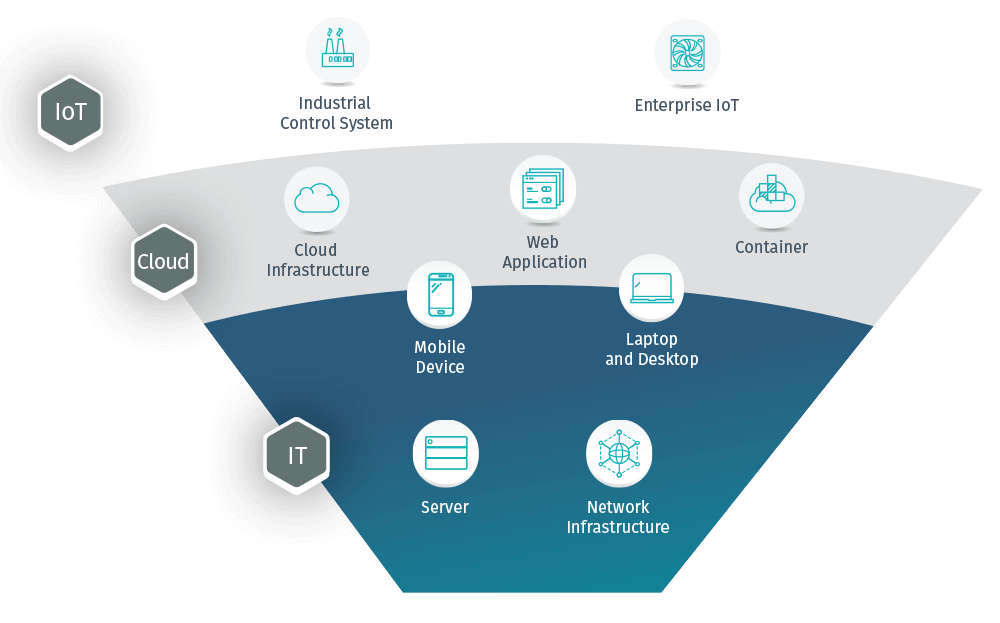
The following sections will demonstrate in detail the services IDS team provides to contribute in managing and mitigating cyber threats and risks
Addressing the Full Cyber Exposure Lifecycle
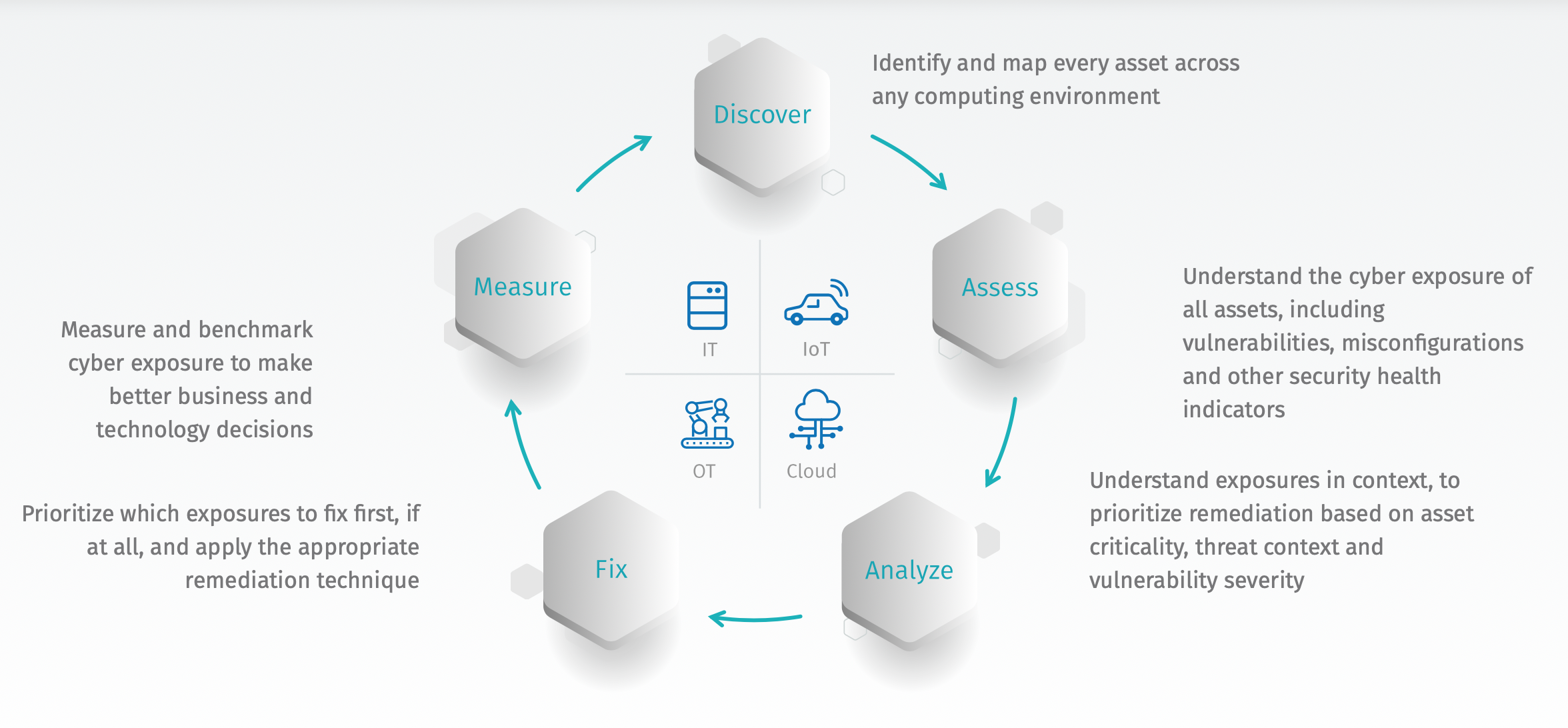
Cyber Risk Management
- Identifying possible threats and risks
- Identifying critical systems, networks and data that are essential for business continuity
- Establishing the necessary cyber security technologies
- Designing a risk mitigation strategy to foster cyber resilience and avoid any implications that could be caused by breaches
- Providing industry-focused advice and guidance on data management and security
Privileged Identity and Access Management
- We assist you in implementing access rights according to the specific responsibilities of each member of your organization, balancing and distributing the responsibility across each level in your organization, and ensuring cyber security is managed effectively.
- We help you design Privacy Programs and manage them.
- We implement standard practices of identification (i.e. multi-factor authentication)
Incident Response Process Establishment
- Incident Response Process is an important characteristic of our services, where it complements the preventive measures that are placed to ensure your organization’s IT environment is resilient.
- It allows your organization to quickly and efficiently recover damaged systems, effectively mitigate further potential risks that might be posed on your business and communicates to your end-customers how resilient and to what extent they can rely on your business.
Network Security
Business Email Protection
Web Interface Protection
Mobile Application Security
Database Security
Vulnerability Assessment & Remediation Services
With the ubiquitous nature of cyber threats and risks, our teams offer assistance with your organization’s current state of security and privacy. We help you identify your vulnerabilities and weak points in your systems, mitigate and manage the threats and risks associated with them.
Cyber Due Diligence
- Digital Forensics Reports
- Information Security Posture Reports
- Security Policy Consistency
- Malware and Compromise Analysis
- Software Patch Management
- User Behavioral Analysis
Privileged Identity and Access Management
- Identifying valuable assets
- Detecting threats from internal or external aspects
- Discovery of vulnerabilities in business processes and information systems
- Understanding the effects and impact of various threats different scenarios could lead to
- Business Risk Assessment
Cyber Attacks Mitigation and Remediation Services
- Analyze attack vectors of cyber incidents
- Identify incident impact and affected systems
- Assess vulnerable system aspects
- Eradicate cyber threats
- Deception Technology Deployment
Governance Compliance Preparation Services
Whether measured against an accepted cybersecurity framework, a standard or regulation, or an industry benchmark, it is essential in today’s cyber risk landscape that organizations have a clear outlook into the level of cyber maturity of their organizations so that adjustments can be made to bring their cyber hygiene in line with the cyber threat and compliance landscape.
- Compliance Certification Preparation Services
- Governance Policies and Procedures Development
- Awareness and Training Services
- Insider Threats and Cyber Security Hygiene
- Assuring Regulatory Awareness
- Secure Software Development and Deployment
- Understanding Role of Cyber Governance
- Board Level
- CXO Level
- Executive Management Level
- Employee Level
- Holistic Approaches Preparation
- Technical considerations
- Human considerations
- Physical considerations
Third Party Risk Assessment & Management Services
An organization cannot rely only upon its own personnel to act in a compliant and ethical manner. Undoubtedly, the actions of an entity’s third-party stakeholders, including agents, partners, representatives, intermediaries, suppliers, and vendors, can have a dramatic impact on the security visibility, operational efficiencies, legal obligations and liabilities and brand reputation of the entity.
Consequently, it is necessary for organizations to ensure that their third-party stakeholders also implement and manage compliance and ethics programs that address the risk areas and issues that have an impact on the organization.
IDS helps clients design and establish third-party cyber and privacy risk management programs, and conducting risk assessments and due diligence.
Our teams have extensive experience in:
- Designing and implementing third-party risk mitigation strategies, policies, and processes
- Reviewing, designing, creating, implementing, and improving vendor and supplier codes of conduct
- Establishing procurement frameworks that specify security expectations for bidders and for purchasing staff, including language suitable for RFPs, RFQs, RFIs, and contractual SLAs
- Conducting common-framework-based assessments (i.e. ISO, PCI, HIPAA) on third parties
Mergers & Acquisitions (M&As) Cyber Due Diligence
By 2022, Gartner reports that 60% of organizations engaging in M&A activity will consider cybersecurity posture as a critical factor in their due diligence process, up from less than 5% in 2019.
Increased enterprise interests in expansion and growth, local and global, has created a spree of M&As across the world. Buying another company means taking on its digital operations, which can pose potentially deal-altering IT and cyber risks. The risks for a buyer [and investing organization] in this environment are increasing. How a company protects its data, intellectual property and technology are all crucial for confirming its value to an acquirer.
IDS meets these demands by delivering a wide range of expert due diligence activities on overall IT and cybersecurity posture. In a world of increasing pressure to move quickly to complete an acquisition, time is of the essence. Although cybersecurity diligence may require more investment and time during the process by the acquiring company, a M&A that analyzes all the cybersecurity issues in advance is likely to have a better overall outcome and encounter fewer surprises along the way.
Our teams assist buyers in mitigating IT and cyber risks during their M&As activities by focusing due diligence activities on target companies’:
- Historical Records of IT and Cybersecurity Breaches
- Cybersecurity Programs
- Third-Party Security Risk Management Policies
- Security Controls for Protection and Detection
- Security and Privacy Controls for IP Protection
- Data Privacy Policies
Cybersecurity plays a greater role in M&A strategy than it did previously, and it can even be a deal-breaker in certain circumstances. An acquirer needs to be able to identify and quantify those issues and either push the target to address them before closing or renegotiate the price and possibly other terms.
IDS provides effective cyber due diligence processes that yield a clear road map for buyers the critical concerns and issues’ remediation cost and suggested timeline for resolving each of them. This gives buyers and investing organizations the visibility to make informed decisions and negotiate fair values of target companies.
Our team of seasoned professionals helps in mitigating IT and cyber risks during M&A activities effectively by swiftly conducting assessment, inventory and diligence activities on target companies through:
- Defining technology assets (hardware and software)
- Assessing network infrastructures
- Evaluating systems’ configuration
- Outlining systems and policies for data management and storage
- Identifying both sides’ systems’ compatibility and integration possibility

